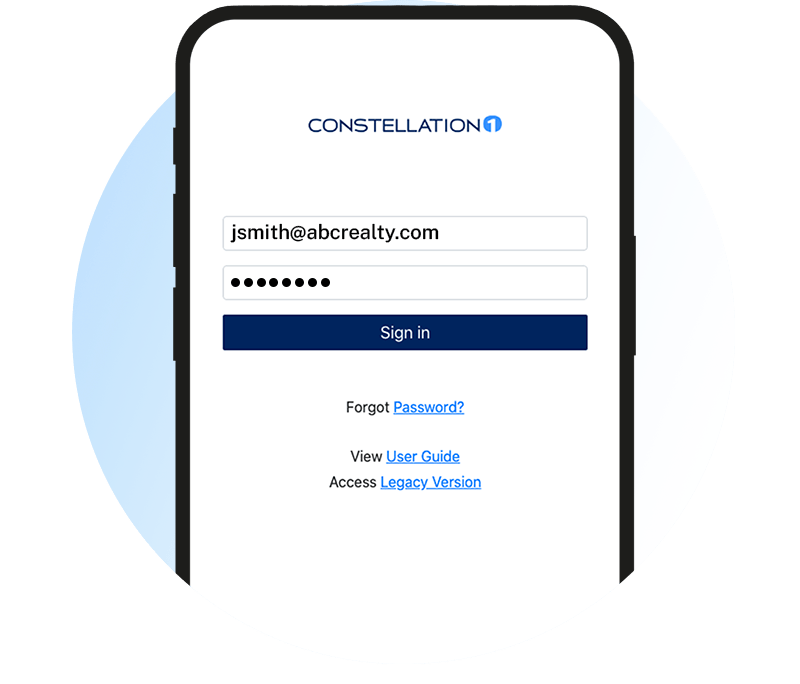
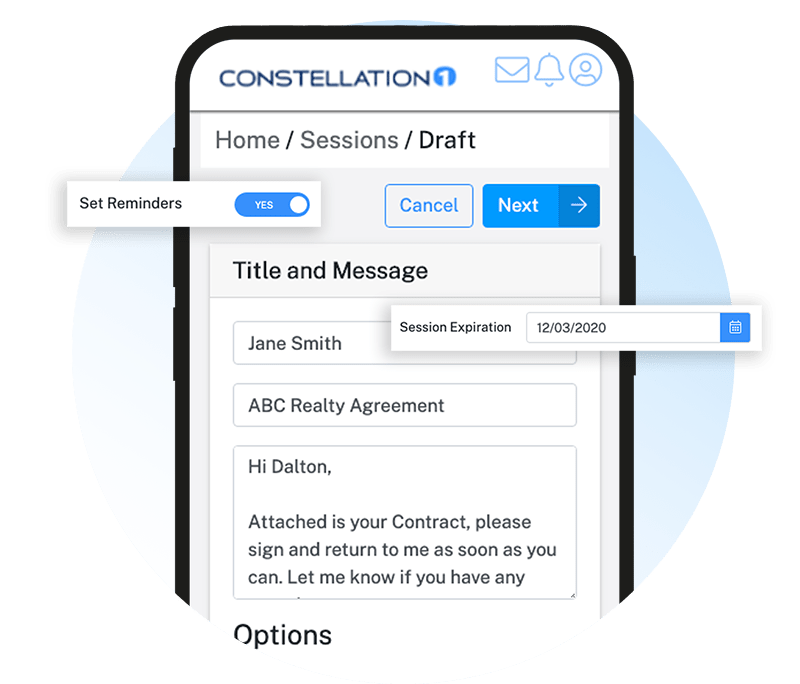
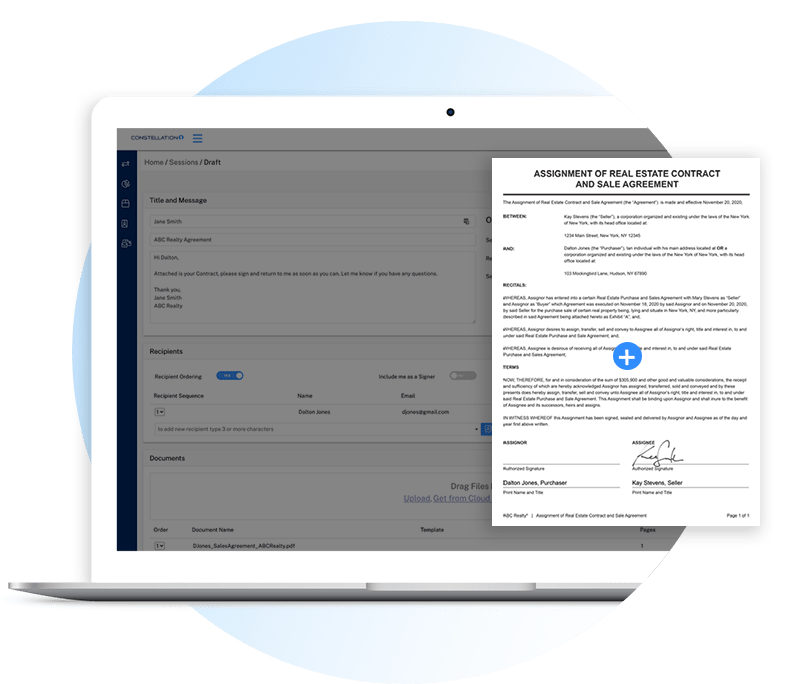
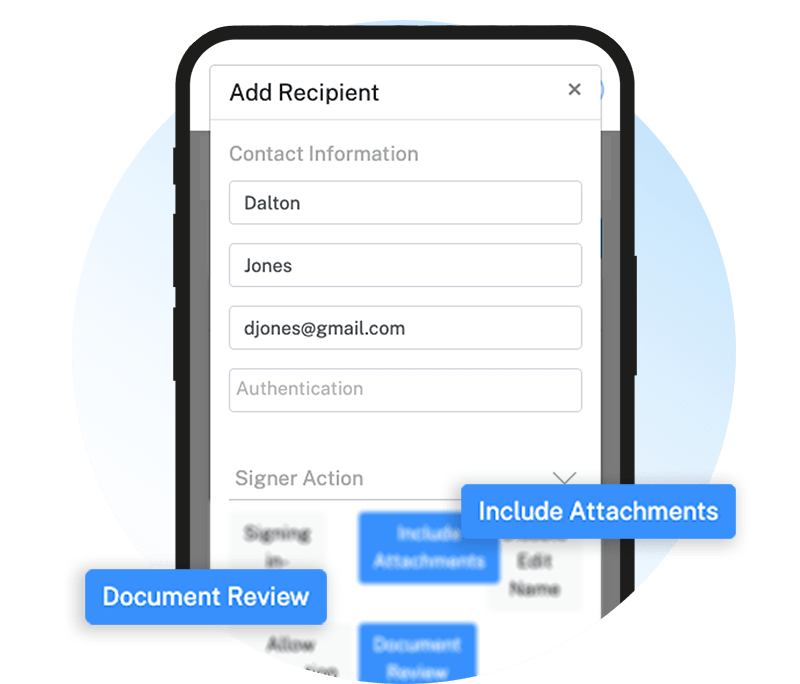
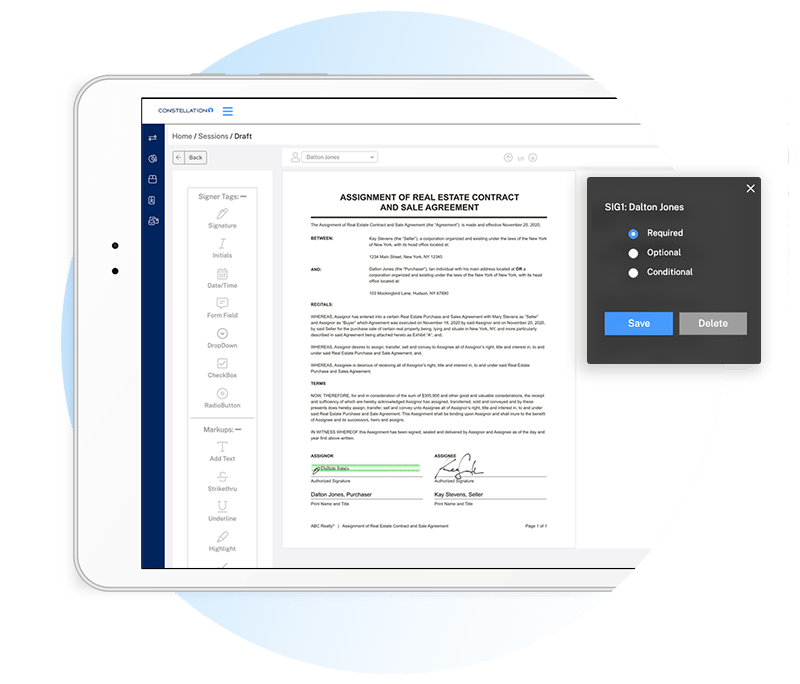
Easily send, sign, and manage all your contracts in one place
Keep business moving. Simplify and accelerate processes with flexible workflows for all of your agreements.
Key features
Secured Sessions
- Session secured to Federal government standards
- Ability to password protect signing sessions
- Audit log tracks session activity
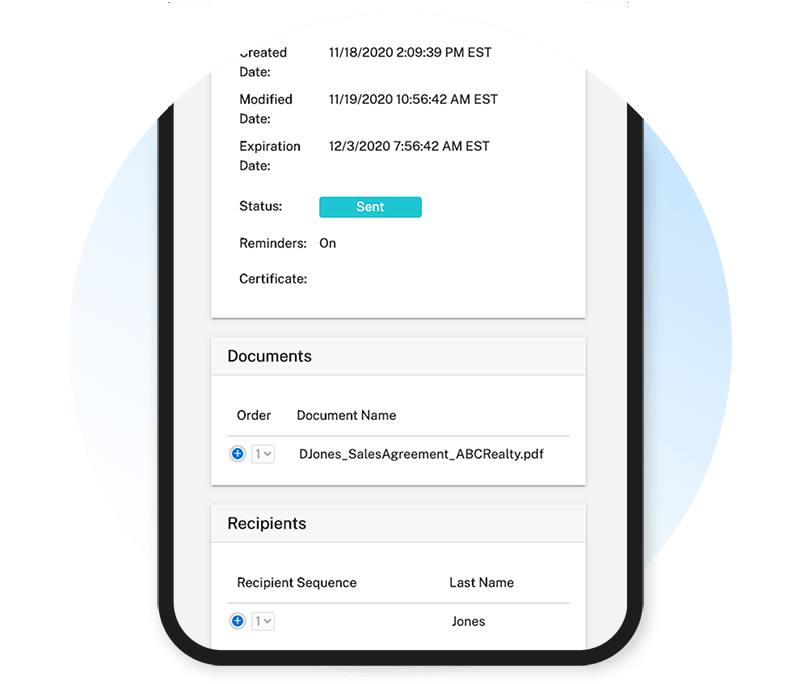
Secured Storage
- Online access to documents
- Documents stored for up to 6 months
- Access executed contracts anytime
Share Documents
- Integrates with Box, Dropbox & Google Drive
- Send docs from any platform

Custom Branding or White Label
- Customize branding
- Customize email templates
Customizable Templates
- Create your own template
- Customize forms with signing locations for signature, initials, and dates.
API
- Direct integration and single sign-on options
- Access API Documentation
Improve Customer Experiences
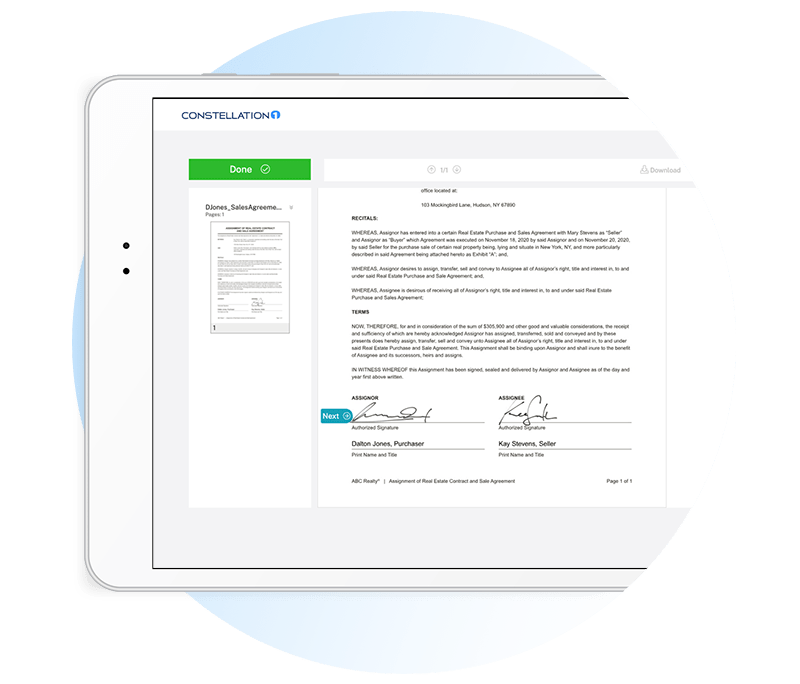
Complete signing sessions from anywhere
Security and compliancy with Electronic Signature Laws
Intuitive and easy to use
Ready to Get Started
Our client success team will meet 1 on 1 with you every step of the way from onboarding to implementation.

 Free Trial
Free Trial